How does cyber security relate to your AML system?
Inherently, as a financial institution doing business every day, you capture sensitive data about your customers. That sensitive data includes customer, account, and transaction data, and is housed in your Anti-Money Laundering (AML) system, if not other places as well. Your accounting system is likely well protected from insider fraud and internet attacks, but your AML system may be an unlocked door to the same data if it is not similarly protected. If you are vulnerable to these risks, your company could be responsible for breaches of confidentiality, lose customers and money, or be subject to lawsuits. This is one way we believe cyber security relates to AML. This article will define what the threat to your AML system and what steps you can take to further protect it through policies, procedures and programs, such as a SSL certificate
business every day, you capture sensitive data about your customers. That sensitive data includes customer, account, and transaction data, and is housed in your Anti-Money Laundering (AML) system, if not other places as well. Your accounting system is likely well protected from insider fraud and internet attacks, but your AML system may be an unlocked door to the same data if it is not similarly protected. If you are vulnerable to these risks, your company could be responsible for breaches of confidentiality, lose customers and money, or be subject to lawsuits. This is one way we believe cyber security relates to AML. This article will define what the threat to your AML system and what steps you can take to further protect it through policies, procedures and programs, such as a SSL certificate
The scenario
 Every day, you sit down and log in to your AML system to run reports or check alerts. Do you know how that data gets to you? Just in case you don’t, let’s make sure. Your sensitive data exists in two different states, Data-At-Rest and Data-In-Flight. Data-At-Rest is the data stored in your AML server or your PC. Data-In-Flight is the data as it travels between these locations, whether you are querying a transaction or updating customer information. The cyber security vulnerabilities we’re going to discuss, as they relate to AML, are related to Data-In-Flight.
Every day, you sit down and log in to your AML system to run reports or check alerts. Do you know how that data gets to you? Just in case you don’t, let’s make sure. Your sensitive data exists in two different states, Data-At-Rest and Data-In-Flight. Data-At-Rest is the data stored in your AML server or your PC. Data-In-Flight is the data as it travels between these locations, whether you are querying a transaction or updating customer information. The cyber security vulnerabilities we’re going to discuss, as they relate to AML, are related to Data-In-Flight.
Threats
Local Hosting
If your AML system is hosted locally, that means it is usually on-site at your institution or a branch of your institution and is managed and monitored by your IT department. However, just because your AML system is hosted locally, typically on an intranet or remote access such as a VPN network, does not necessarily make it safe by that alone. According to an article written by Tracy Coenen, a forensic accountant and fraud investigator, "Companies are most at risk of fraud from their employees, since they have access to information and assets" (Coenen, 2014). Since your AML system holds sensitive data which includes your customer, account, and transaction data, it would be proactive to take every measure possible to make sure it is as secure as possible. As previously discussed, when your sensitive data travels from the AML server to your computer it is referred to as Data-In-Flight. Data-In-Flight is usually transferred in "cleartext", meaning it is readable to anyone who can view it. Data-In-Flight is vulnerable to programs such as Packet Sniffer’s, which may be placed on your network by a rogue employee or a hacker during a network breach. A Packet Sniffer copies the data as it travels between the AML server and your computer, and if the data is not encrypted, whoever controls the Packet Sniffer may now have access to your sensitive data.
Remote Hosting
In a scenario where your AML system is hosted remotely simply means that your server is hosted by a vendor who hosts it on their network on your behalf. The most common way to connect your desktop to their network is through a dedicated line. As data flows from your desktop to the server, it is Data-In-Flight. Threats to this data are increased by this additional connection via the dedicated line. In addition to your data residing in a different location and travelling, you are now subject to the policies and procedures of the hosting company, which may be less secure than your policies. If this sounds like your institution, you’ll want to make sure that your vendor is providing you their policies and procedures, and reporting on how often they’re scanning their servers for Packet Sniffers and the like.
The cost of compromised data
The average cost to a company after a data breach is $3.5 million and rising (Ponemon Institute, 2014). It can be gleaned that the more customers you have, the more it costs when there is a breach. However, that is only the cost of investigations, notifications, and responses. This amount does not include losses related to customers leaving due to lack of confidence, or falling stock prices.
How you can prevent this
With the proper policies, procedures, and programs, you can minimize the risk of data breaches to your business.
Policies and Procedures
How can you help yourself in the battle against data thieves? Tracy Coenen recommends that, "…companies invest in a comprehensive fraud prevention program. This will cost money up front, but that investment is easily recovered by a reduction in the company’s fraud risk." Policies and procedures, when followed by all employees, make it difficult for hackers and rogue employees to gain access to your sensitive data, which makes you a much less tempting target.
 There are also some important questions that you’ll need to consider:
There are also some important questions that you’ll need to consider:
- Is there a strong password policy in place?
- Do you require that passwords change periodically?
- Is your company insured against data theft/breach?
- Do you have multi-authentication or challenges in place?
- Is the data breach procedure in your Business Continuity Plan up to date? See Memorandum 07-16 from the Office of Management and Budget (OMB) for outlining a breach procedure. (Johnson, 2007).
- Has there ever been a risk analysis based on data breaches performed?
- Is there a procedure in place to deactivate employee logins and revoke access to the AML system when an employee changes departments or leaves the company?


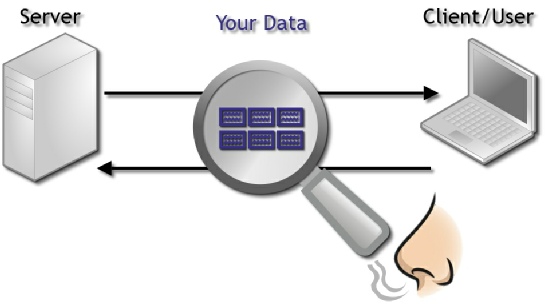
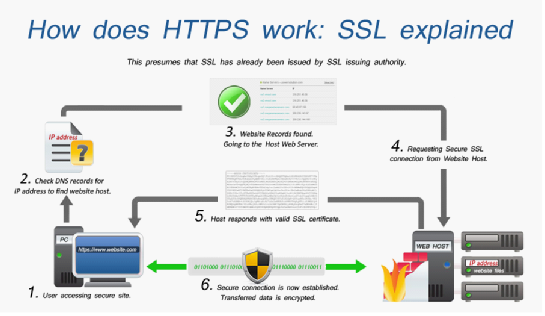 Image Credit: Dadian, 2013
Image Credit: Dadian, 2013